Comprehensive Cybersecurity for Microsoft 365
In today’s digital landscape, safeguarding your organization’s data and ensuring seamless operations are paramount. Our cybersecurity services for Microsoft 365 environments are designed to provide robust protection against evolving threats, ensuring your business remains secure and compliant.
Why outsource the management of your cybersecurity?
Many internal IT/Security teams are capable of managing an organization’s cybersecurity tools.
The question is, should they be doing this?
Industry experts agree, this is something that every organization should outsource to cybersecurity specialists who can monitor your systems in real-time, 24 hours a day; stay up-to-the-minute on emerging threats; and who are well-versed in responding to potential threats. When a cyber incident happens, experience always wins over tools and training.
Outsourcing to a dedicated managed security provider ensures a proactive stance, with specialists who holistically analyze data from all sources, constantly adapt to new attack vectors, and have their “ears to the ground” on the ever-evolving threat landscape. This allows your internal teams to focus on strategic initiatives and core business functions, while the experts handle the heavy lifting of cybersecurity—around the clock, without pause.
Why Forthtright Cyber?
- Advanced Threat Protection: We leverage cutting-edge technologies to detect and mitigate sophisticated cyber threats, including phishing, malware, and ransomware, before they can impact your operations.
- Data Loss Prevention: Our solutions ensure that sensitive information is protected from unauthorized access and accidental leaks, maintaining the integrity and confidentiality of your data.
- Identity and Access Management: We implement stringent identity and access management protocols to ensure that only authorized users have access to critical resources, reducing the risk of insider threats.
- Compliance and Governance: Stay compliant with industry regulations and standards. Our services include regular audits, policy enforcement, and reporting to ensure your Microsoft 365 environment meets all necessary compliance requirements.
- 24/7 Monitoring and Support: Our dedicated team of cybersecurity experts provides round-the-clock monitoring and support, ensuring that any potential threats are swiftly addressed and your systems remain secure.
- User Training and Awareness: Empower your employees with the knowledge and tools they need to recognize and respond to cyber threats. Our training programs are designed to enhance security awareness and foster a culture of cybersecurity within your organization.
Implementation is usually simple. Our team of experts will implement the necessary security measures, integrating seamlessly with your existing Microsoft 365 environment to enhance protection without disrupting your operations.
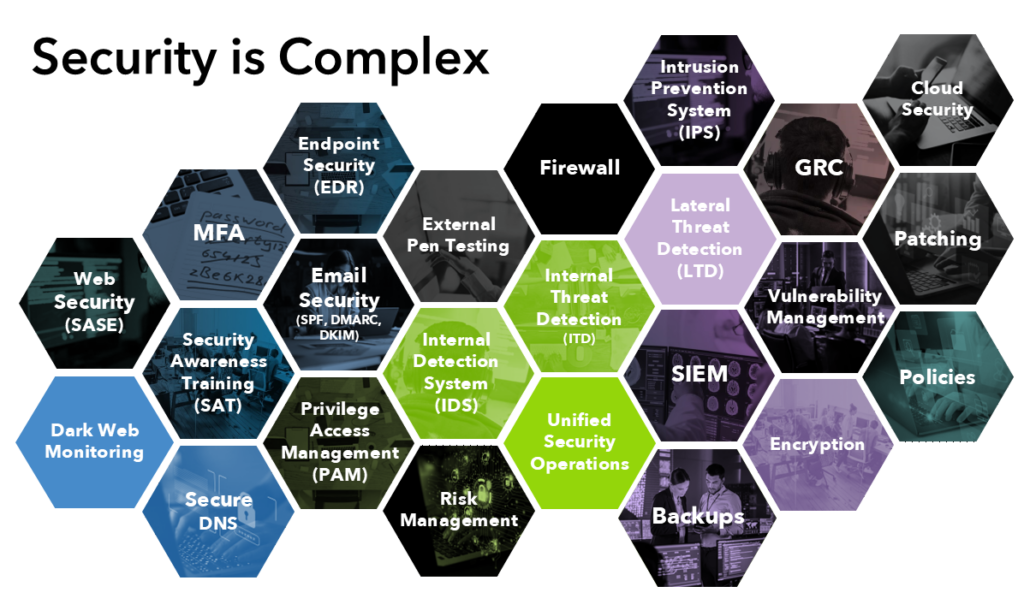
Navigating the Complexities of Modern Cybersecurity
Tools aren’t enough
No single tool can handle all cybersecurity tasks. Even with multiple tools, it’s crucial to have dedicated personnel to manage and monitor them around the clock. This includes securing endpoint devices, patch management, monitoring alerts, resetting alarms, assessing tool effectiveness against evolving threats, and analyzing numerous incidents to identify suspicious activities requiring deeper scrutiny.
Before your organization starts buying cybersecurity tools, consider a comprehensive, proactive approach to cybersecurity. Forthright Cyber brings expertise, continuous monitoring, and the latest threat intelligence, ensuring your defenses are always up-to-date and effective. Our holistic services not only save time and resources, but also provide peace of mind knowing that a dedicated team is handling your security needs, allowing you to focus on your core business operations.
Contact Us Today
They say there are two types of companies that don’t have a robust cybersecurity program: those who have been hacked and those who don’t know they have been hacked. Don’t leave your cybersecurity to the unknown. Partner with Forthright Cyber and take proactive steps to protect your Microsoft environment.
Contact us today to learn more about our Managed Security Services for M365 and how we can help safeguard your digital assets.
Book a Meet With Our Team
or Click Here to Contact Us