Cyber Series on Identity and Access Management Episode 11: User Authentication (part 2 of our IAM series)
In the ever-evolving landscape of cybersecurity, understanding the foundational principles that govern information security is crucial. One such framework that continues to be a cornerstone is the CIA Triad: Confidentiality, Integrity, and Availability. These three principles are essential in protecting data and ensuring that organizations operate securely.
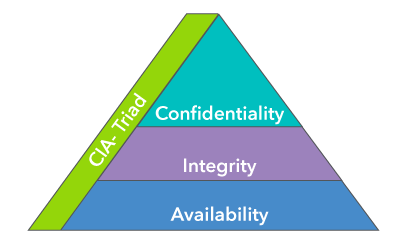
The CIA Triad: A Refresher
- Confidentiality ensures that sensitive information is only accessible to those who are authorized. It’s about maintaining privacy and protecting data from unauthorized access.
- Integrity focuses on maintaining the accuracy and completeness of data. Think of it as ensuring that the information hasn’t been tampered with, and keeping a revision history is an excellent example of preserving integrity.
- Availability ensures that authorized users can access the information they need when they need it. This principle is crucial for business operations, as downtime can be costly.
These pillars are the bedrock of information security, and identity and access management (IAM) plays a vital role in ensuring they are upheld. By properly identifying, authenticating, and granting access, businesses can maintain the principles of the CIA triad effectively.
Conditional Access: Strengthening Identity Management
A key component of IAM is conditional access—a security process that controls access based on user signals like identity and location. Conditional access is particularly relevant in environments like Microsoft’s M365 and Entra ID systems. Although not all organizations may have access to every feature, many can leverage this powerful tool to better secure their environments.
Conditional access works by verifying both who the user is and where they are accessing the system from. This is crucial in preventing unauthorized access, especially when employees may be working from various locations around the globe.
Moving Beyond Passwords: The Rise of Multi-Factor Authentication
The conversation around passwords has shifted dramatically in recent years. While passwords were once seen as a primary defense mechanism, they are now recognized as a weak point. Bill Burr, the author of the original NIST password guidelines, admitted that much of the early password advice was overly complicated and not entirely effective.
In today’s environment, passwords alone are no longer enough. Multi-factor authentication (MFA) is the gold standard, requiring at least two factors for authentication. These could be:
- Something you know (e.g., a password or PIN),
- Something you have (e.g., a physical device like a phone or security key),
- Something you are (e.g., biometric data like fingerprints or facial recognition).
For example, using an ATM requires both your card (something you have) and your PIN (something you know), making it a basic form of MFA.
Types of MFA: Not All Are Created Equal
While most of us are familiar with basic MFA techniques like receiving a code via text message, this is actually one of the least secure methods. Higher-strength MFA methods include passwordless options such as biometric authentication (fingerprints or facial recognition), security keys like YubiKeys, or authenticator apps like Microsoft Authenticator. These methods offer a much more robust defense against phishing and other attacks.
Secure Passwordless Authentication
Passwordless authentication is a growing trend, offering options like:
- Biometric authentication, such as fingerprints or facial recognition.
- Passkeys, which are tied to specific devices and often combined with biometrics for an additional layer of security.
- Security keys, physical devices that can be plugged into a computer to authenticate the user.
These methods are significantly harder to compromise than traditional passwords and help ensure that only authorized users gain access to critical systems.
Enhancing Security with Location Signals
Location-based security is another crucial aspect of conditional access. By identifying and limiting access to specific geographic locations, businesses can further secure their data. For example, you can block access from countries where your business doesn’t operate or allow more restrictive access to sensitive applications like your accounting system.
Looking Forward: What’s Next?
As businesses continue to evolve their IAM strategies, it’s important to stay ahead of the curve. Future discussions in our Cyber Series will delve into topics like device compliance, risk monitoring, and data governance. By adopting a comprehensive approach to identity and access management, businesses can protect themselves from threats while improving operational efficiency.
Want to learn more about how conditional access, MFA, and passwordless authentication can improve your security posture? Contact Forthright today for more information or tune in for future Cyber Series on Identity and Access Management episodes.
Written by forthright on October 15, 2024 Under Cybersecurity, Tech Insights