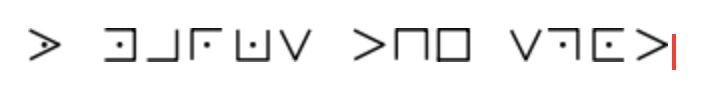A Guide to Encryption: History, How It Works, and Why You Need It
Some folks believe that encryption, which is the process of encoding information or data to prevent unauthorized access to the information, was first developed and used as computers were first being invented. For example, it’s argued that the first computer was actually the Turing Machine. If you know some history, you know that it was developed by Alan Turing in 1963 and used in World War II to help the Allied Forces decipher German military codes, which aided in defeating the Germans.
When was encryption actually invented?
Encryption was actually invented and used way before World War II. As a matter of fact, encryption is a process that was in use as early as 1900 BC in ancient Egypt. All forms of encryption require the use of a key in order to decrypt the encoded message. The original message is also known as plaintext, as this is in a human readable form.
Over the years, there have been many types of encryption ciphers used to encode information, which used substitution or transposition/permutation techniques; each using specific keys to encode and decode messages. A substitution cipher is one in which the letters in the original message are substituted for other letters.
Here’s an example…
One of the simplest, most popular substitution ciphers is known as the Caesar Cipher, which got its name from Julius Caesar who used it to communicate with his generals. In this cipher, letters in the original message are shifted a certain number of places down the alphabet to produce the encrypted message. The key used for this cipher is the number of spaces that each letter is shifted down the alphabet.
Here’s the alphabet in order as we know it:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
If we use the Caesar Cipher, this means that A becomes C, B becomes D, C becomes E and so on. Encoding the word “HELLO” using this cipher would become “JGNNQ”. If I didn’t know what key to use, then deciphering this could take me a while. Of course, with the advancement in computing power, such a simple cipher can be broken in seconds.
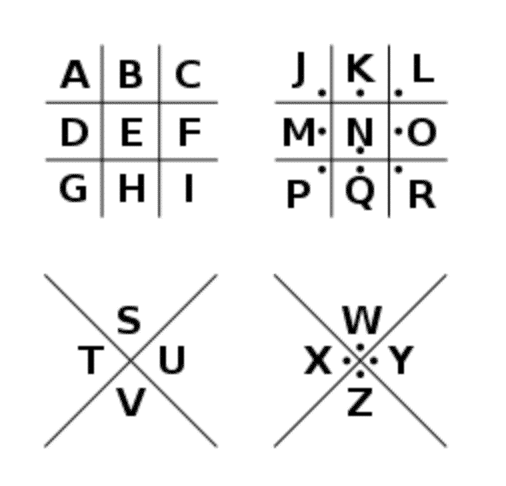
Here’s another fun cipher using the substitution technique called the Pig Pen cipher, see if you can figure out what the original message is.
Here’s the encoded message:
And here’s the key:
Let’s take a look at the transposition or permutation technique. Unlike the substitution cipher, in which letters are substituted or shifted as defined by the key, in a transposition cipher, the key itself is a permutation.
Ok, so what’s a permutation?
Here’s the definition:
“A way, especially one of several possible variations, in which a set or number of things can be ordered or arranged. “ – dictionary.com
Instead of trying to explain further, here’s an example:
For this example, the key is going to be a permutation of the letters ABD, in which A represents position 1, B represents position 2, and D represents position 3. I will order it in this way: BAD or 213
The original message or plaintext will be: “The quick brown fox jumped over the lazy dog.”
Here’s how the original message is encoded:
- Since there are 3 letters in the key, I will create a grid that has 3 columns and write out the letters of the plaintext under the columns like so:
| B | A | D |
| 2 | 1 | 3 |
| T | H | E |
| Q | U | I |
| C | K | B |
| R | O | W |
| N | F | O |
| X | J | U |
| M | P | E |
| D | O | V |
| E | R | T |
| H | E | L |
| A | Z | Y |
| D | O | G |
- Next, I rearrange the columns so that the numbers are in order. We get:
| A | B | D |
| 1 | 2 | 3 |
| H | T | E |
| U | Q | I |
| K | C | B |
| O | R | W |
| F | N | O |
| J | X | U |
| P | M | E |
| O | D | V |
| R | E | T |
| E | H | L |
| Z | A | Y |
| O | D | G |
- And finally, I write out the letters to get the encoded message: (notice that spaces are not included in the encoded message, and that all the letters of the plaintext were not changed, just reordered)
“HTEUQIKCBORWFNOJXUPMEODVRETEHLZAYODG”
Again, a modern computer could break this code in a matter of milliseconds, but the points that I am trying to make here are:
- The different techniques that an encryption cipher can use.
- The fact that the key is the most important part for encrypting and decrypting a message for a given encryption method.
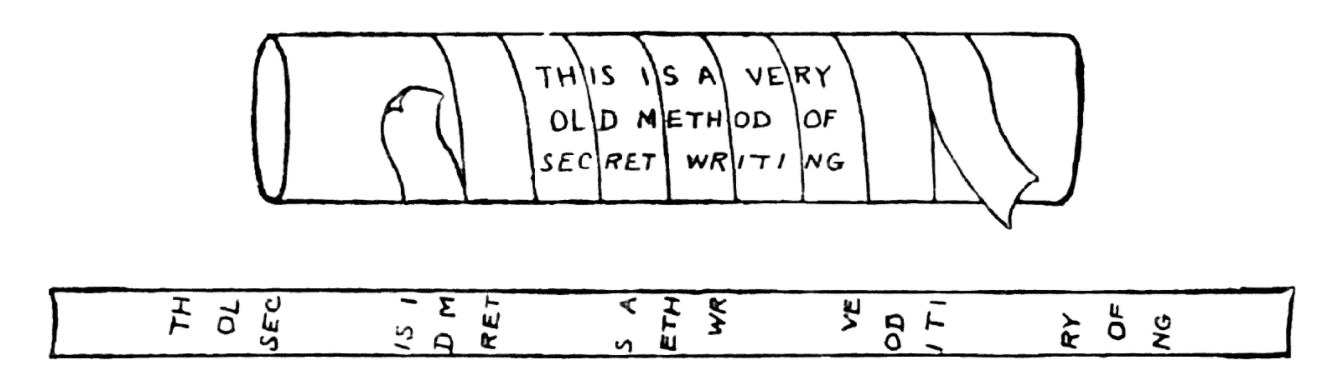
Here’s another interesting transposition cipher: The Scytale Cipher.
The Scytale Cipher was used in ancient Greece by the Spartans in which a band was wrapped around a rod, and a message was written. When the band was unwrapped, an encoded message would appear. To decode the message, a rod of the same width and diameter had to be used.
Here’s an image to help you visualize the concept:
The key here would be the size of the diameter and length of the rod used. A different diameter and length would produce a different readout of. So let’s talk more about encryption keys.
What are encryption keys?
In the world of encryption, there are two types of keys, symmetric and asymmetric keys.
Symmetric keys use the SAME key for both encryption and decryption, in comparison to Asymmetric keys, which use two different keys for encryption and decryption but are derived from the same mathematical formula.
Symmetric key encryption is much faster than asymmetric key encryption.
I won’t get into the specifics of which scenarios each are used for in this article, but I will get into a little more detail in my next blog.
In any case, for ALL of the encryption examples that I have used thus far, I have used Symmetric keys. This means that the key I used to encrypt the original messages, is the same key that I needed to decrypt the encoded message. So, if I sent you an encoded message using the Caesar cipher and a key of 5, (more commonly known as a Rotation Cipher and denoted as ROTx, in which ‘x’ identifies how many spaces the letters are rotated or shifted down the alphabet. So for this example it is ROT5), the only way for you to decrypt my message is if I also give you the key or told you that it was using ROT5.
But what if I was in some city in Iran and you were located in Miami FL, and I sent you an encoded message to warn about an ISIS invasion… How would you know how to decode it unless you had the key? How could I risk sending you the key along with the message and trust that no one would intercept my message AND the key? I couldn’t.
If my message were to be intercepted by enemy spies, they would also have the key and it would be as though I was just sending the original non-encoded message. This is where the concept of key exchange comes in.
I will end here for now, but I will get more into key exchange, when and where Symmetric Key and Asymmetric Key encryption is used, and the concept of PKI or Public Key Infrastructure in my upcoming articles.
Get started with encryption now…
If this inspired you to start protecting your sensitive accounts and/or services with encryption, get in touch with us…
- Book a meeting with me, our cybersecurity expert, to talk more about encryption
- Find out which encryption service is right for you
- Enjoy peace of mind knowing anything confidential will be unreadable